| Materials to be Covered in Class | Class Presentations | Current Events | General Information |
Class Materials
The Twitter Timeline
The final exam.
Mr. Boal's slides.
 Privacy and Security Privacy and Security
- Jeffrey Rosen - Is Privacy Dead?
- Virus and Trojan Horses
- Facebook's Eroding Privacy Policy: A Timeline
- Privacy and Social Networks
- A Look at Cookies
- Firefox and Privacy
- How Viruses Work
- Hacking Tip: Forge email addresses
- Viruses, Bots, and Phish, �Oh My!
- Some tools
- ·Spybot
- ·AdAware
- ·AVG
- ·McAfee
- ·Norton Tools
- ·SpamBayes
- ·Snopes
 Green Computing Green Computing
- Mr. Weber's presentation
- Wikipedia's definition
- IBM's Green Computing
- Microsoft's Green Computing
- IEEE's Green Computing
- EcoSeed's Green Computing
- Information Week's Green Blog
Google hackers duped system administrators to penetrate networks, experts say
Google Is Blocked In 25 Of The 100 Countries They Offer Products In
The Open Net Initiative: Global Internet Filtering
Google releases data on governments' demands for user data, site censorship
 Web Design Web Design
- Check out everyone's websites!
- Working with CSS
- Tables revealed: my home page
- Design Issues
- Design Techniques
- More on Cascading Style Sheets
- Documentation
<i>Page Owner:</i> <a href="http://www.umsl.edu/~sauter/">Professor Sauter</a>
(<a href="mailto:Vicki.Sauter@umsl.edu">Vicki.Sauter@umsl.edu</a>)<br>
<SCRIPT LANGUAGE = "JavaScript">
// This automatically updates the last modified date for the page.
//
when = document.lastModified
document.write("<i>This page was last modified on:</i> " + when + "<br>")
//
// This automatically updates the location documentation on the page.
where = document.location
document.write("<i>URL:</i> " + where)
</script>
<br>
© Vicki L. Sauter. All rights Reserved.
|
- HTML Primer
- Research-Based Web Design and Usability Guidelines
- ·Design Process and Evaluation
- ·Optimizing the User Experience
- ·The Homepage
- ·Navigation
- ·Web Content
Midterm grades
For discussion: Court limits FCC clout over Web (implications for net neutrality) and Ruling could reshape regulation of broadband Internet
 Security Security
FTC poised to gain stronger hand in making rules with financial reform bill
Cyber Insecurity: U.S. Struggles To Confront Threat
Listen to the story
From ACM's Tech News, April 19, 2010
Scientists Work to Keep Hackers Out of Implanted Medical Devices
CNN (04/16/10) Sutter, John D.
Researchers are developing ways to prevent hackers from accessing and remotely controlling medical devices that emit wireless signals. For example, Oak Ridge National Laboratory's Nathanael Paul is designing a more secure insulin pump that cuts some of the wireless connections between parts of the system. Other researchers are looking for security solutions for pacemakers and cardiac defibrillators. Some researchers have suggested protecting the devices with passwords, but doctors and nurses would have to be able to control the devices in the case of an emergency. "If you have a patient that's unconscious on the ground, you really don't want the medical staff to have to figure out what security system they're using," said University of Washington's Tamara Denning at the recent CHI 2010 conference. The passwords could be tattooed in the form of a barcode on the patient's skin, either with visible ink or ink that can only be seen under ultraviolet light, Denning said. Security issues for medical devices will increase when these devices are connected to phones, the Internet, and other computers, notes University of Massachusetts at Amherst professor Kevin Fu.
View Full Article
Keeping Medical Data Private
Technology Review (04/13/10) Gammon, Katharine
Vanderbilt University (VU) researchers have developed an algorithm designed to protect the privacy of medical patients while maintaining researchers' ability to analyze large amounts of genetic and clinical data. Although patient records are anonymized, they still contain the numerical codes, known as ICD codes, which represent every condition a doctor has detected. As a result, VU professor Bradley Malin says it is possible to follow a specific set of codes backward and identify a person. Malin and his colleagues found that they could identify more than 96 percent of a group of patients based only on their particular set of ICD codes. To make patients more private, the researchers designed an algorithm that searches a database for combinations of ICD codes that distinguish a patient and then substitutes a more general version of the codes to ensure each patient's altered record is indistinguishable from a certain number of other patients. The researchers tested the algorithm on 2,762 patients and could not identify any of them based on their new ICD codes.
View Full Article
 Outsourcing Outsourcing
Professor Rottman's slides
The World is Flat 3.0
Global outsourcing of back office services: lessons, trends, and enduring challenges: Dr. Rottman
would like you to read it before he speaks.
 The midterm. The midterm.
 Open Source Open Source
Life after Windows: What happens to tech if Microsoft dies.
The Open Source lecture. now links to the revised presentation
The Cathedral and the Bazaar: referenced in the talk.
 From ACM's Tech News, April 7, 2010
Making Voting Systems Open Source Could Forever Change Election Technology From ACM's Tech News, April 7, 2010
Making Voting Systems Open Source Could Forever Change Election Technology
Government Technology (03/30/10) Collins, Hilton
- The nonprofit Open Source Digital Voting (OSDV) Foundation is developing a suite of open source election software that allows users to see and tweak the underlying computer code, which advocates say enables a global expert community to assess the code's security and make positive changes. OSDV's Greg Miller says that eight U.S. states are engaged in the foundation's Trust the Vote project, and custom, modular tools might be necessary to address different jurisdictions' various requirements and needs. Customization will be built into the OSDV's suite, which could prove essential in the extremely scattered voting system market. Miller says the foundation's goal is to have all of its election elements in place and a system that is ready for federal certification by the time of the general election in 2016. ODSV developers already have built an online open source voting registration tool, and a series of Web-based data management services are either deployed or in the prototype phase.
View Full Article
 Cloud Computing Cloud Computing
Ms. Shoptaw's presentation.
The video Ms. Shoptaw showed.
Steve Ballmer on Cloud Computing.
Gartner report on Cloud Computing
A satirical look at Cloud Computing: perhaps not politically correct, but it does provide a challenging view to cloud computing.
Information Assurance practices of Cloud Computing Vendors
Service-Oriented Architecture: Myths, Realities, and a Maturity Model: This article is not about cloud computing specifically, but rather
about software as a service (you'll remember Ms. Shoptaw talked about it as SOA). The researchers note that many who have gone to this approach were looking for an architectural initiative, not as a business transformation tool.
 The Internet The Internet
CNN broadcasted a simulation on Sunday called "We Were Warned: Cyber.Shockwave," which hosted former
members of the executive branch of the federal government who "played" members of the Cabinet and associated people.and their deliberations
on what to do in response to a cyber attack. It is worth seeing, and YouTube is hosting the show in nine parts. View
first part and then follw the links to the other eight segments. We will not watch it in class,
but I want you to watch it.
Internet Lecture 1
Internet Lecture 2
We briefly touched on e-government issues last week. Here is a short article that summarizes on how to make it work. Most of it applies to business as well.
See the Business Week article about Google Broadband; you can nominate St. Louis to be one of the cities
Facebook
See New York Times article
LinkedIn Advice by Dwayne Miller.
More about LinkedIn
Motivations for Social Networking at Work
Twitter
Getting Started with Twitter
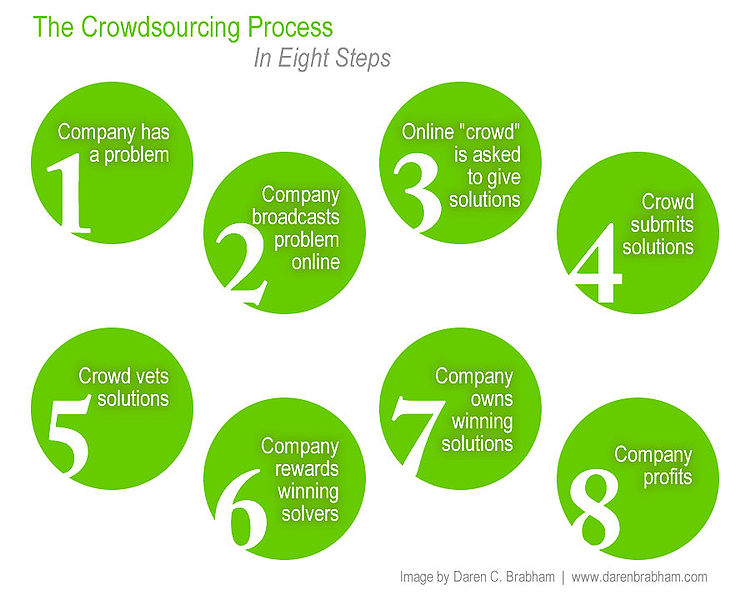
Crowdsourcing
·Examples of Crowdsourcing
·From ACM's TechNews, January 29, 2010
How Crowdsourcing Is Helping in Haiti
New Scientist (01/27/10) Mullins, Justin
The revolution in texting, social networking, and crowdsourcing has enabled innovations such as the 4636 texting service, which is aiding the disaster relief efforts in Haiti by recruiting scores of volunteers to help translate messages that could mean the difference between life and death. Another crowdsourcing initiative is CrisisCommons, which has organized thousands of volunteers to enhance the map of Haiti available on the open source OpenStreetMap site. Other projects CrisisCommons is spearheading include one to build a Craigslist-style "we need, we have" Web site to connect people offering resources to those that need them. The proliferation of mobile communications infrastructure to the developing world has supported the emergence of new tools for using text messaging, run by relatively small organizations that can work fast using limited resources in difficult conditions. This places them in a pivotal position as facilitators of disaster relief. Individuals and organizations have been galvanized to collaborate via social networking media by the realization that large-scale activities can be coordinated through online networks.
View Full Article
·'Citizen cartographers' map the microcosms of the world
Blogging
 Smart blogging can boost your career Smart blogging can boost your career
 Pope to priests: For God's sake, blog! Pope to priests: For God's sake, blog!
Web 2.0
 Tutorial: Introduction to Web 2.0 Tutorial: Introduction to Web 2.0
 Engineering Viral Success Engineering Viral Success
A definition of the Internet (during the 2006 debate of Net Neutrality)
Senator Steven's original statements about the Internet
the Daily Show's commentary on Steven's definitions.
John Hodgman's interpretation of Steven's view and net neutrality
The Conservative's Case for Net Neutrality
Social Network References
NetLab
 Overview of Information Systems Overview of Information Systems
The new version of the key issues for executives has been published: Key Issues for IT Executives 2009: Difficult Economy's Impact on IT
Federal CIO Vivek Kundra
Chapter 1 Powerpoint slides
Does IT Matter?
Why Study MIS?
Carr's webpage
a New York Times article
USA Today article
John Hagel's response
IT Still Doesn't Matter
The Evolution of Removable Storage
Class Presentations
Security and Cyber Crime
Malware
Phishing
Cyber Crimes
Denial of Service Attacks
Malware
Phishing
CyberBullying
Internet Use Presentation
Airline Industry
Automotive Industry
Beer Industry
Furniture Business
Retail Stores
Sports Media
Television Industry
Topics in IS Presentations
Business Week
CIO
FastCompany
New York Times
Washington Post
Wired
ZDNet
Interesting Current Events
 Security Issues Security Issues
From ACM's TechNews, April 16, 2010
At Internet Conference, Signs of Agreement Appear Between U.S. and Russia
New York Times (04/15/10) Markoff, John
Security specialists from eight countries met at a Russian-sponsored conference on Internet security to discuss their differences on how governments view cyberspace. "The Russians have a dramatically different definition of information security than we do; it's a broader notion, and they really mean state security," says U.S. ICANN representative George Sadowsky. Russian officials note the two nations agreed to restart bilateral discussions that commenced in Washington last November. White House cybersecurity official Christopher Painter cites substantial improvement in international law enforcement cooperation in recent years, and stresses that strong laws, trained crime investigators, and efficient global cooperation are necessary to respond to cyberspace-based challenges. For years the United States and Russia have repeatedly refused to sign cybersecurity and/or cybercrime pacts offered by either side. But there have been encouraging signs at the recent conference. In a panel discussion on computer crime, the former chief counsel of the U.S. National Security Council and an official with the Russian Interior Ministry concurred that removing anonymity is the most crucial step in fighting Internet crime.
View Full Article
Exposing Hackers as an International Deterrent
Technology Review (04/13/10) Talbot, David
An international group of computer scientists, law professors, military leaders, and others recently met at Russia's Moscow State University for a conference on methods of deterrence for online hackers. Naval Postgraduate School computer scientist James Bret Michael argued that surveillance on computer networks and other forms of intelligence can provide the clues needed to expose a potential hacker, and this exposure may often serve as a deterrent. Retired Russian general Vladislav Sherstuyuk announced a new research collaboration consisting of government officials from Russia and China, as well as academic institutions including the Indian Institute of Information Technology, Allahabad, and the State University of New York (SUNY) at Albany. The agreement will "undertake common research on international information security," Sherstuyuk says. The collaboration reflects an increased international concern over the potential devastation that computer attacks can cause. "The U.S. needs to work with Russia because it is one of the hotbeds of crime and hacker activity," says SUNY Albany computer scientist Sanjay Goel.
View Full Article
Dismantling of Saudi-CIA Web site illustrates need for clearer cyberwar policies
I received the following email from my local police department on March 17, 2010.
| According to a recent study from the Javeline Strategy and Research Group, Identity Theft increased by 12.5 percent in 2009. According to James Van Dyke, founder of the research group, these numbers will increase "As the economy gets more challenging and more and more people are out of work."
Now is the time to be more vigilent with your personal information and securing your credit. One of the simplest ways to detect Identity Theft and fraud is to check your financial statements. Every month, promptly check your statements to ensure that all charges are legitimate and were made by you. If there is a doubt, you need to contact your bank promptly to start the dispute process.
Check your credit report annually. The only place to obtain a free credit report is at www.annualcreditreport.com. This is a web site established by the credit reporting agencies that enables you to get 1 free credit report in a 12 month period from each agency. You can complete the forms online, or request a report by calling 877-322-8228, or writing to Annual Credit Report Request Service, P.O. Box 105281, Atlanta, GA 30348-5281. Claims made by companies to protect you from identity theft could be a ruse. In fact, the Federal Trade Commission recently settled a $12 million lawsuit with LifeLock, a company who made false claims about protecting consumers from identity theft.
To deter identity theft and financial fraud you should also follow these suggestions:
- -Protect your social security number
- -Shred any trash/mail that has identifying information on it
- -Use the internet carefully; only purchase items from trusted, secure web sites
- -Verify a source before you give them ANY personal information
For more information on Identity Theft and financial fraud, visit the Federal Trade Commission's web site (www.ftc.gov) or the Missouri Attorney General's web site (www.ago.mo.gov).
|
From Good Experience, March 17, 2010.
|
Over-sharing: problems with social networking and privacy
Just a tip that "over-sharing" is a topic coming soon to your favorite media source. The story goes like this: with the rise in popularity of social networks (Facebook, Twitter, Flickr, etc.), users have been encouraged to share - usually publicly, with the world - all sorts of data about themselves, their relationships, and their activities. But now some people are beginning to question whether they should post their entire life online. Maybe there's such a thing as over-sharing your information.
Several things have contributed to this growing awareness of over-sharing. One of my recent favorites is a site called Please Rob Me, which showed the notices of users on Foursquare, a service that lets you post publicly, to the world, the restaurant or bar you're standing in right then. In other words, Please Rob Me showed you hundreds of people announcing that they were away from home. As the site says today (and it has since stopped showing the Foursquare feed), "If you don't want your information to show up everywhere, don't over-share."
It would seem to be a common-sense suggestion: think before you share something publicly. (Do people really want to know this? Is it actually helpful? Relevant? Are there any tradeoffs or potential drawbacks from sharing it with the entire world?)
The problem is, the social-networking sites don't do much to ask these questions. To the contrary, they're set up to encourage users to share as much as possible, as often as possible, as publicly as possible. That's intentional: these sites succeed by increasing the activity within the network. Yes, there are privacy settings to limit access to some data - but these settings are never the default. Only a tiny minority of users make the effort to opt out. Everyone else shares with the world.
Today the Times reported on the amount of personal data that can be gleaned from smart data-mining on social networks. While an interesting finding, I don't think it's even necessary to go that far: just browse around on practically any Web 2.0 site to see the incredibly personal information that people post. I'm just waiting for a site to launch where people enthusiastically display their birthdates and Social Security numbers because, y'know, everyone's doing it.
Don't misunderstand me: I like the social networking sites. I have accounts with most of them and post fairly frequently on my Twitter and Facebook feeds, which you're welcome to subscribe to. But I try to adhere to some common-sense boundaries about what's relevant and OK to share, and what's off-limits.
Much like the other skills of bit literacy, this boundary-setting is the responsibility of the users, since the companies don't have much to gain from encouraging it. I hope the coming discussion about over-sharing will help nudge users in the right direction.
|
From ACM's Tech News, March 17, 2010.
How Privacy Vanishes Online
New York Times (03/16/10) Lohr, Steve
Personal privacy is being threatened as Internet users increasingly provide information about themselves on social networking sites, which can be collected and analyzed by computers to create a picture of a person's identity. "Personal privacy is no longer an individual thing," says Massachusetts Institute of Technology professor Harold Abelson. "In today's online world, what your mother told you is true, only more so: people really can judge you by your friends." Although users can implement privacy controls on most Internet sites, researchers say that is rarely enough to protect privacy. For example, University of Texas professor Viatly Shmatikov and Stanford University researcher Arvind Narayanan were able to identify more than 30 percent of users of both Twitter and Flickr, even thought the accounts had been stripped of identifying information like account names and email addresses. At Carnegie Mellon University, researchers Alessandro Acquisti and Ralph Gross reported they could accurately predict the Social Security numbers for 8.5 percent of the people born in the United States between 1989 and 2003--nearly 5 million people. "When you're doing stuff online, you should behave as if you're doing it in public--because increasingly, it is," says Cornell University professor Jon Kleinberg.
View Full Article
How Secure is your Data?
White House declassifies outline of cybersecurity program
German court overturns law on phone, e-mail data
From ACM's TechNews, February 24, 2010
Experts Warn of Catastrophe From Cyberattacks
CNet (02/23/10) Mills, Elinor
A panel of experts told U.S. senators at a recent hearing of the Senate Committee on Commerce, Science, and Transportation that the United States would be defeated in an all-out cyberwar, and reducing this vulnerability will not occur until the government takes a more active interest in safeguarding the nation's network. Former director of national security and national intelligence Michael McConnell warned that greater government involvement may not happen until after a "catastrophic event" transpires. The focus of the hearing was the Cyber Security Act of 2009, which would oversee organizations and companies that supply critical U.S. infrastructure, mandate licensing and certification for cybersecurity professionals, and sponsor grant and scholarship programs.
View Full Article
From ACM's TechNews, February 17, 2010
War Game Reveals U.S. Lacks Cyber-Crisis Skills
Washington Post (02/17/10) P. A3; Nakashima, Ellen
The Bipartisan Policy Center recently staged the Cyber ShockWave, a simulation to demonstrate the plausibility of a cyberattack that could be as crippling as the Sept. 11, 2001, terrorist strikes. "We were trying to tee up specific issues that would be digestible so they would become the building blocks of a broader, more comprehensive cyberstrategy," says former CIA director Michael Hayden. The simulation, in which the cell phones and computers of tens of millions of Americans were turned into weapons to shut down the Internet, had 40 million people in the eastern United States without electrical power and more than 60 million cell phones out of service. Privacy was a key stumbling block in any strategy the participants tried to put forth. "Americans need to know that they should not expect to have their cell phone and other communications be private--not if the government is going to have to take aggressive action to tamp down the threat," says Jamie Gorelick, a former deputy attorney general. Participants also wrangled over how far to go in regulating the private sector, which owns the vast majority of the "critical" infrastructure that is vulnerable to a cyberattack.
View Full Article
Large worldwide cyber attack is uncovered
U.S. pinpoints code writer behind Google attack: report
China is world leader in hacked computers, report finds
From ACM's TechNews, February 12, 2010
China Alarmed by Security Threat From Internet
New York Times (02/11/10) LaFraniere, Sharon; Ansfield, Jonathan; Markoff, John; et al.
China is increasingly worried about threats to its security and political stability posed by the Internet. Both Chinese and U.S. political analysts and technology experts say China's attempts to tightly control the Internet are partly fueled by the conviction that the West is trying to foment unrest in China and weaken the country from a military standpoint through the use of a wide range of communications innovations. U.S. experts say China's cyberdefenses are more riddled with holes than those of the United States. New policies are being set up to replace foreign hardware and software with domestic systems, while officials also are broadening the reach and resources of state-controlled media outlets so they reign over Chinese cyberspace with their blogs, videos, and news. Unrest in Xinjiang and elsewhere, allegedly stoked by online warfare from the West, has prompted Chinese leaders to step up new efforts, including the closure of thousands of Web sites, tightening censorship of text messages for objectionable content, and planning a convergence of China's Internet, phone, and state TV networks. They also are nurturing domestic alternatives to foreign computer technologies and foreign-based Web sites such as YouTube, Facebook, and Twitter.
View Full Article
Federal Government Builds Secret Database to Fight Cyber-Terrorism
Computerworld Australia (02/11/10) Pauli, Darren
Australia's federal government has been given sensitive data from utilities, banks, and other organizations for the Critical Infrastructure Protection Modeling and Assessment (CIPMA) program. "Identifying, tracking the cascading effects of [critical infrastructure (CI)], and quantifying these consequences is a key rationale for establishing the CIPMA program," says a spokesperson from the Federal Attorney General's department. "Direct relationships with industry means that there is a high level of trust to enable the provision of accurate data for modeling and analysis." Approximately 4 TB of CI data will be warehoused in central databases, making it unnecessary to retrieve information from knowledge experts who may not be accessible in a disaster. System dynamic models are employed to analyze stock and flow data in CI, such as network connectivity and the energy output of generators, to produce an amalgamated output to be fed into a People, Building, and Infrastructure profile. Data is then deconstructed into demographic, economic, and business profiles, and into statistical divisions to generate novel disruption footprints. The CIPMA program is one of numerous actions that authorities have recently taken to counter increasing numbers of cyberthreats.
View Full Article
Security
·Annual Threat Assessment of the US Intelligence Community for the Senate Select Committee on Intelligence
·National Cybersecurity Alliance
·Tech China Ties Coming Under Scrutiny
·From ACM's TechNews, February 1, 2010
UN Calls for Global Cyber Treaty
Australian Associated Press (AAP) (02/01/10)
·International Telecommunications Union Secretary-General Hamadoun Toure says the world is moving closer to seeing nations go to war over a cyberattack and an international accord is needed before that happens. "The framework would look like a peace treaty before a war," Toure says. Nations would guarantee to protect their citizens and their right to information, promise not to harbor cyberterrorists, and agree not to launch an attack on another country. Although former U.S. intelligence director John Negroponte says the intelligence community would balk at a global cyberaccord, U.S. Sen. Susan Collins (R-Maine) says the prospect of a war over a cyberattack is now being considered in the United States. Microsoft's Craig Mundie says at least 10 countries could carry out sophisticated attacks that could appear to come from anywhere. Other experts say that about 20 countries are in a cyberspace arms race and are preparing for possible hostile actions over the Internet. "People don't understand the scale of criminal activity on the Internet," Mundie says. "Whether criminal, individual, or nation states, the community is growing more sophisticated."
View Full Article
From ACM's TechNews, January 29, 2010
E-Passports Threaten Your Privacy
University of Birmingham (01/19/10) Chapple, Kate
University of Birmingham (UB) researchers have discovered a flaw in e-passports that makes them susceptible to identification. The defect is in the design of the radio-frequency identification tag used by e-passports. The discovery makes it possible to detect the passport of a particular person from a distance of a few meters. An attacker can track the movements of a specific passport by replaying a particular message. "Our discovery has shown that there is a flaw that makes it possible to identify the movements of a particular passport without having break the passport's cryptographic key," says UB researcher Tom Chothia. E-passports have been issued to more than 30 million people.
View Full Article
In Digital Combat, U.S. Finds No Easy Deterrent
Depressing Analysis Of RockYou Hacked Passwords
Analysis of 32 million breached passwords
FBI's Investigative Programs: Cyber Investigations
Hillary Clinton calls for Web freedom, demands China investigate Google attack
China attacks Clinton's Internet speech as 'harmful' to relations
The Lock That Says 'Pick Me'
In War Against the Internet, China Is Just a Skirmish
Google and China
Far-Ranging Support for Google's China Move
After Google's Stand on China, U.S. Treads Lightly
For Google, a Threat to China With Little Revenue at Stake
Google China cyberattack part of vast espionage campaign, experts say
Hey, Look, It's The Twitter Fail Whale!
 Computer Help for Haiti Computer Help for Haiti
Technology as a Lifeline During Natural Disasters
From ACM's TechNews, January 29, 2010
Haitians in Crisis: Developing Translation Tools
Carnegie Mellon News (01/27/10)
Scientists at Carnegie Mellon University's Language Technologies Institute (LTI) have released spoken and textual data on Haitian Creole that will help groups in their efforts to develop translation technologies for relief workers in Haiti. Microsoft has already used the data to develop a Web-based system for translating between English and Haitian Creole. LTI researchers began to update their own translation system for Haitian Creole after the Jan. 12 earthquake, but decided that releasing its data to the public would lead to faster development of translation tools. The French nonprofit Translators Without Borders is working on a medical triage dictionary for doctors in Haiti. LTI's Robert Frederking says there are few translation resources for Haitian Creole, which is based on the French language and incorporates African syntax. "Nobody is going to make money on a Haitian Creole translator," Frederking says. "But translation systems could be an important tool, both for the relief workers now involved in emergency response and in the long-term as rebuilding takes place."
View Full Article
From ACM's TechNews, January 22, 2010
Tech Volunteers Aiding Haiti Relief Efforts
InformationWeek (01/20/10) Hoover, J. Nicholas
Software developers and tech-savvy individuals from around the world are organizing to help with the Haiti relief effort. For example, Noel Dickover co-founded CrisisCommons to provide non-governmental organizations (NGOs) and others in Haiti with better information and situational awareness. "If we can improve situational awareness and information sharing, we can help NGOs have better performance across the board," Dickover says. Projects already underway include the Haiti OpenStreetMap, a global positioning system-compatible street map of Haiti. Another project is the We Have, We Need Exchange program, an online marketplace for the exchange of resources and services geared toward NGOs in Haiti. Other projects include a timeline of events, a wiki hosted by National Public Radio, an English to Creole dictionary for iPhone and Android mobile devices, and a system to use Twitter messages to ask for or offer assistance. Other volunteer tech efforts include a collaborative effort between Ushaahidi, InSTEDD, and Thompson Reuters to launch a disaster information service using local SMS short code for people in Haiti to text their emergency needs. Read the article. View the Open Street Maps of Haiti.
Quake mobilizes D.C. area to help Haiti
Crisis Commons: an international volunteer network of professionals drawn together to create technological tools and resources for responders to use in mitigating disasters and crises around the world.
 The Internet The Internet
Turkey blocking 3,700 websites, reform needed: OSCE
Facebook Valued At $14 Billion On SecondMarket
NASA Astronaut Tweets From Space ? For Real This Time
 The Field The Field
Are There too Many IT jobs or too Many IT Workers?
 Green Computing Green Computing
From ACM's TechNews, February 12, 2010
NTU Launches One of the World's Greenest Supercomputers
Nanyang Technological University (Singapore) (02/11/10) Ang, Esther
Nanyang Technological University (NTU) researchers recently launched the High Performance Computing (HPC) Centre, which features sustainability features such as the use of water-cooled technology that reduces electrical consumption by 30 percent. The HPC Centre also reduces electricity consumption by automatically adjusting to specified energy-usage levels and transaction speeds. NTU's supercomputer is ranked as the sixth most energy-efficient in the world based on the x86 architecture. New research areas for the system include developing future energy sources, studying global climate change, designing new materials, and understanding biological systems. "The establishment of the supercomputer brings under one roof a centralized large-scale computing facility to the 2,800-strong research community on campus," says NTU's Bertil Andersson.
View Full Article
General Information
Laptops For Kids
5 Simple Tools for a Paperless Office
From ACM's TechNews, April 16, 2010
Interview: Wendy Hall on What Web Science Could Mean for Businesses
Computer Weekly (04/12/10) Thomson, Rebecca
University of Southampton professor Wendy Hall, who is involved in the newly founded, Internet-focused Institute of Web Science, says the interdisciplinary field is experiencing rapid growth as governments increasingly acknowledge the value the digital economy will bring to the developed world in the coming decades. Among the disciplines that make up Web science are economics, law, sociology, philosophy, and technology. Hall says Web science will concentrate on the Internet's potential impact, especially as it begins to transform into the Semantic Web thanks to a new generation of services and businesses. She notes that the public sector is spearheading the transition to a "linked" or data Web rather than academia or industry. As an example of the kinds of services enabled by the Semantic Web, Hall cites an application called Asbometer, which integrates geographical data and information on anti-social behavior orders to supply a service showing how many people have such a disorder in a specific region. She stresses that businesses need to keep pace with Web developments, given the potential for upheaval similar to the inversion traditional business models experienced with the advent of the first version of the Web.
View Full Article
Researchers at TAU Claim Computerized Voting System Unsafe
Ha'aretz (Israel) (04/15/10) Shtull-Trauring, Asaf
Tel Aviv University (TAU) researchers have found major flaws in a new computerized voting system that has been proposed to replace ballot boxes in Israeli elections. The researchers say the system does not protect against sophisticated attempts to forge and falsify votes. Adopting the new computerized voting service would present a danger to democracy, says TAU professor Avishai Wool. The proposed system uses a voting computer and a smart card. Voters receive an empty smart card, hold it up to the computer, and select the desired candidate. After voting, they insert the smart card into the ballot box. Election officials would then verify if there is a discrepancy between the figures recorded by the computer and those in the smart cards. The researchers disrupted the system's functions by erasing information using several different methods. "We succeeded in disrupting the computer from a distance of two meters in the laboratory," Wool says. However, government officials say that anyone seeking to disrupt the voting system would need large amounts of energy in the immediate vicinity of the computer. Johns Hopkins University professor Avi Rubin notes that "computer scientists have for some time succeeded in demonstrating that electronic voting systems are not safe."
View Full Article
A Pulitzer Winner Gets Apple’s Reconsideration
Web Coupons Know Lots About You, and They Tell
the Waze
Comparing the details of various wireless service plans
Scammers getting scammed
InfoWorld Home / Applications / Slideshows / The 10 coolest experiments from Google Labs
The 10 coolest experiments from Google Labs
PC Maintenance: What Tasks When?
Laptop Buying Guide: Shopping Tips
| |