It is previously predominant algorithm for the encryption of a electronic data.It was highly influential in the advacement of modern cryptography in the academic world.Developed in the early 1970s at IBM and based on an earlier design by Horst Feistel
Data Encryption Standard
- -DES is a feistel cipher
- -Block Length is 64 bit
- -Key Length is 56 bit
- -No of rounds are 16
- -Each round is applied on one Block Cipher
- -Security depends primarly on "s-boxes"
- -Each S-boxes maps 6 bits to 4-bits
Objectives
- Block cipher
- Full Size cipher and Partial key cipher
- Components of a Modern Block Cipher
- -P Box (Permutation Box)
- -S Box (Substitution Box)
- -Swap
- -Exclusive OR operation
- Diffusion and Confusion
- Feistel cipher
Two classes of product ciphers
- Feistel ciphers, Example DES(data encryption standard)
- Non-feistel Ciphers, Example AES(Advanced Encryptin system)
Feistel Cipher
Feistel cipher
A Feistel cipher is a symmentric structure used in the construction of block ciphers,named after the German-born physicist and cryptographyer Horst Feistel who did pioneering research while working for IBM (USA);it is also commonly known as a Feistel network.
- A large portion of block ciphers use the sheme,including the Data Encryption Standard
- Feistel structure has the advantage that encryption and decryption operations are very similar,even identical in some cases
- A Feistel network is an iterated cipher with an internal function called round function
- Feistel cipher refers to a type of block cipher design,not a specific cipher
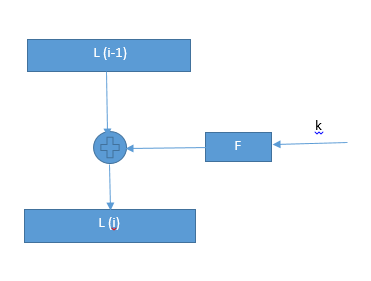
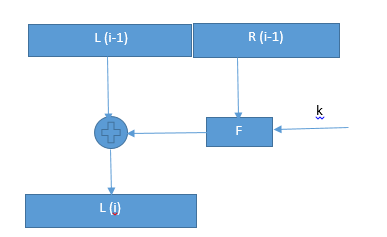
- split plaintext block into left and right halves:Plaintext = (L0,R0)
- For each round i=1,2,......,n compute
- Li = Ri-1
- Ri = Li-1 ⊕ f(Ri-1,Ki)
- where f is round function and Ki is a subkey
- Ciphertext = (Ln,Rn)
- -Now they came with this structure .The round function is a combination of both Ri-1 and Key
- -So we need Ri-1 at the decrypting side so they directly the results of the Ri-1 to the next step
- -Again they found other problem?
- Here comes the swap operation we have discussed earlier

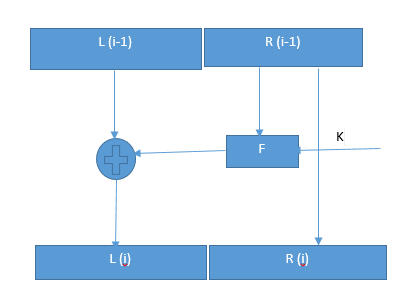

Decryption in fiestal cipher
Block cipher
- As the name suggests here the block of data is encrypted
- Typically block of data which is encrypted is 64-bit
- If the data has fewer no of bits than 'n'?
- If the data is not in the multiples of 'n' ?
Padding
- If the data has fewer than 'n' bits,padding must be done to make it 'n' bits
- If the message Size is not a multiple of 'n' bits,then it should be divided with into 'n' bit blocks and the last block should be padded
Full Size Cipher
- Transposition Cipher
- Substitution Cipher
Transposition cipher
Substitution cipher
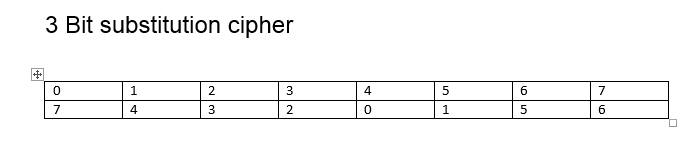
Examples
- Cnsider a 3-bit block ciphers.How many bits are needed for the full-size Key?
- There are 8!=40,320 possible substitutions
- Thus there are ceil(log2(40,320))=16 bits
- Thus it is a permutation of 2n values,thus needs
- ceil[log2(216)]=65,536 bits
- -We can observe there is a lot unused keys.
So what should we do now?
Partial-Size key ciphers
- Actual ciphers cannot use full size keys,as the size is large
- Block ciphers are substitution ciphers(and not transpositions).why?
- -if we use transposition cipher then it will very easy for Attacker to break the code by usng Hamming weight
- -Hamming weight is nothing but no of 1's in a given code
- Example=(101011) Hamming weight is 4
- Consider DES,with 64 bit block cipher.
- -Size of full key=ceil(log2(64!))≈ 270
- -Much large compared to 56 bits which is actually used
- -so we are using partial key cipher
- -here we are considering the 56 bit key for DES

Components of Modern Block cipher
- Most important components are
- -PBOX:It is a key-less fixed transposition cipher
- -SBOX: It is a key-less fixed substitution cipher
- They are used to provide:
- -DIFFUSION:It hides the relationship between the ciphertext and the plaintext
- -CONFUSION:It hides the relationship between the ciphertext and the key
Principle of Confusion and Diffusion
- The design principles of Block Cipher depends on these properties
- The S-BOX is used to provide Confusion,as iti is dependent on the unkonwn Key
- The P-BOX is fixed,and there is no confusion due to it
- But it provides diffusion
- Properly combining these is necessary.
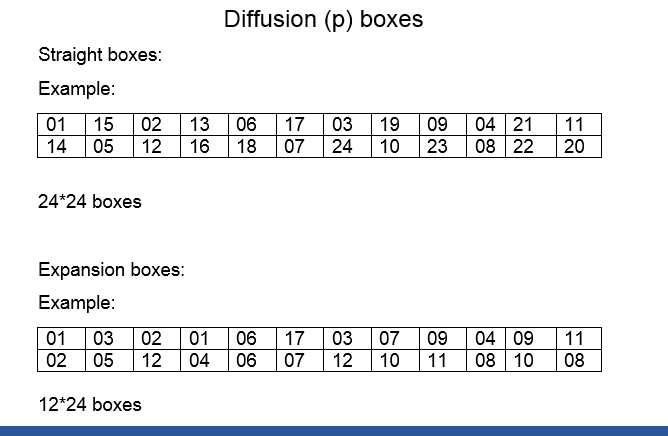
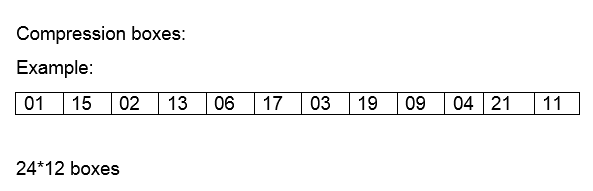
- Diffusion boxes are generally of three types
- How to read this?
- -First bit of the output 01 is derived from the first bit of input
- -It is bijective mapping because there are 24 inputs and 24 outputs
- -In the case of Expansion boxes we have 12*24 means input size is 12 and the output size is 24 so we can see repetition.
- -In the case of Compression boxes we have 24*12 means input size is 24 and output size is 12 so we can see the loss of information
S-BOX
- An S-Box(SUbstitution box) is an M*N susbtitution box where m and n are not necessarily same.
- each output bit is a boolean function function of the inputs.
- y1=f1(x1,x2,.........,xn)
- y2=f2(x1,x2,.........,xn)
- y3=f3(x1,x2,.........,xn)
- .........................
- ym=fm(x1,x2,..........,xn)
- -All the S-boxes should be non-linear
- -Suppose if you consider a bad S-box like Linear.what will happen?
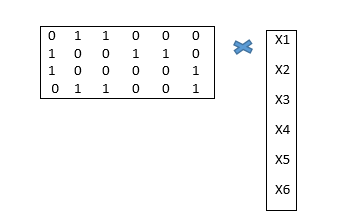
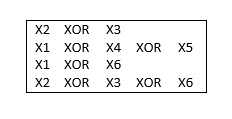
- Si(X1,X2,........,X6)=(X2⊕X3, X1⊕X4⊕X5, X1⊕X6, X2⊕X3⊕X6)
- y1=a11x1 ⊕ a12x2 ⊕ ............ a1nxn
- y2=a21x1 ⊕ a22x2 ⊕ ............ a2nxn
- ...........................
- ym=am1x1 ⊕ am2x2 ⊕ ............ amnxn
- written equivalently: Si=AiX (mod 2)
- -That means we can represent them as form of matrix
- if you do in the same as above the S-BOX just perform XOR operation between various things, permutes and shuffle bits around so it is just XOR's and bit permutations
- As a result all the DES operations would be linear which does not provide security
- From this we can observe only S-BOX operations are non-linear to provide security
- Eg: y1=X1X3 ⊕ X2,Y2=X1X2 ⊕ X3
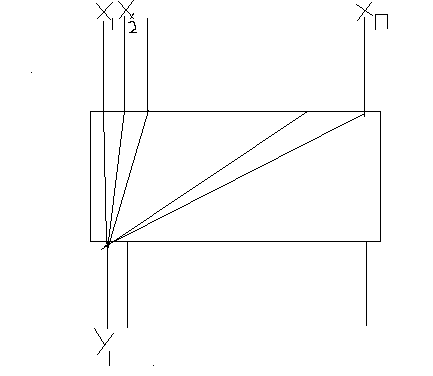
Permutation Box(P-BOX)
- permutation box (or P-box) is a method of bit-shuffling used to permute or transpose bits across S-boxes inputs
Other Components
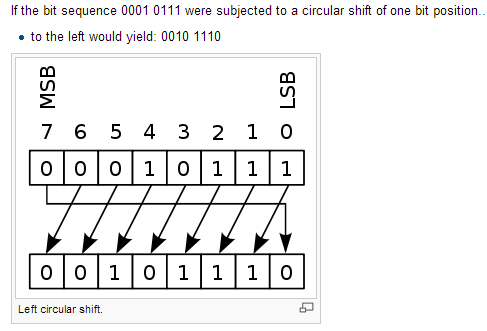
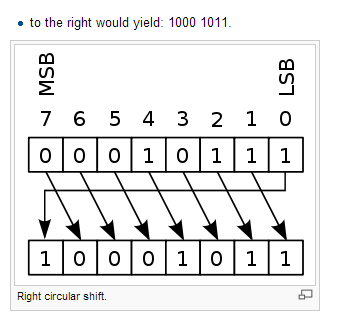
- Circular shift
- -It shifts each bit in an n-bit word K positions to the left.the leftmost k bits become the original rightmost bits.
- -Invertile Transformation
- -For example,repeatedly applying circular shifts to the four-tuple(a,b,c,d) successively gives
- (d,a,b,c),(c,d,a,b),(b,c,d,a),(a,b,c,d)
- Swap
- -A specail type of shift operation where k=n/2
- Other operations involve split and combine
- An important component is exclusive - or operation
Properties of EX-OR
- EX-or is a binary operator,which results in 1 when both the inputs have a different logic.Otherwise,it computes 0
-
- -Symbol ⊕
- Closure:Result of exoring two n bit numbers is also n bits
- Associativity:Allows to use more than one's ⊕ in any order
- - X ⊕ (Y ⊕ Z) = (X ⊕ Y) ⊕ Z
- Comutatavity:X ⊕ Y=Y ⊕ X
- Identity:The identity element is the n bit 0,represented by
- (0,0,0,......0) = 0n
- Thus X ⊕ 0n = X
- Inverse:Each word is the additive inverse of itself
- X ⊕ X = 0n
Application of EX-OR
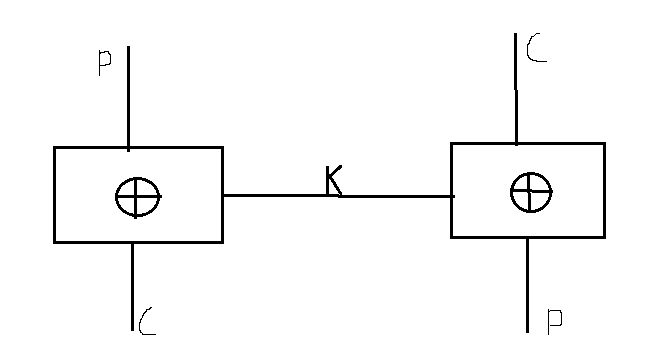
- The key is known to both the encryptor and decryptor and helps to recoer the plaintext.
- C=P ⊕ K
- C ⊕ K = (P ⊕ K) ⊕ K
- = P ⊕ (K ⊕ K)
- = P ⊕ 0n(identity)
- = P
A product cipher made of 2 rounds
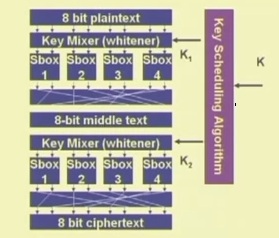
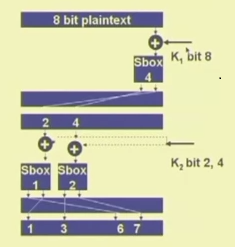
Practical ciphers
- Large data blocks
- More S-boxes
- More rounds
- These help to improve the diffusion and confusion in the cipher