
Use Cases
MISUSE CASES
Let's break something!?
Source = Alexander, I. (2003). Misuse Cases: Use Cases with Hostile Intent.
Source = Alexander, I. (2003). Misuse Cases: Use Cases with Hostile Intent.
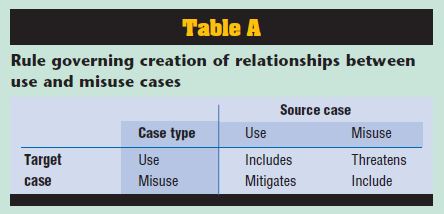
The figure below paints the picture of a use/misuse case of auto theft:
 Source = Alexander, I. (2003). Misuse Cases: Use Cases with Hostile Intent.
Source = Alexander, I. (2003). Misuse Cases: Use Cases with Hostile Intent.
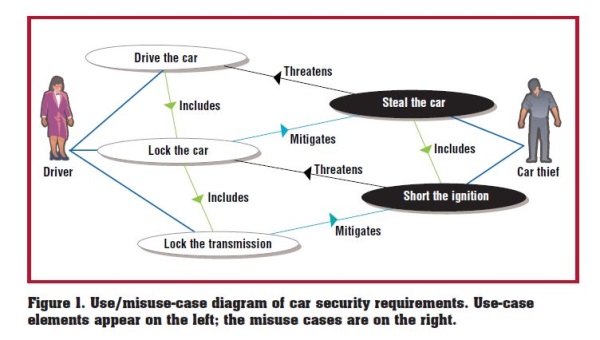
So then, the use case and the misuse case are more akin to opposite sides of a coin. In this manner, both can coexist and solve a matrix of systemic issues. One additional difference concerns the requirements of the solution. In the case of the misuse case, the analyst is looking for scenarios where the system does not solve the problem, but instead could be a creator of the problem, or a reactive agent to an external system (such as weather, below):
 Source = Alexander, I. (2003). Misuse Cases: Use Cases with Hostile Intent.
Source = Alexander, I. (2003). Misuse Cases: Use Cases with Hostile Intent.
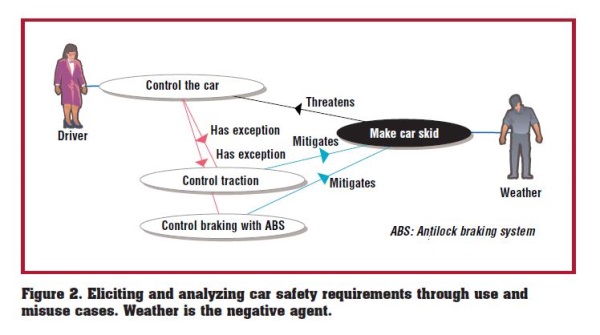
Misuse cases are especially good at finding and describing issues with reliability, maintainability, and other maintenance issues. The misuse case can find "holes" in your use case by virtue of the fact there are no solutions for the misuse scenario.
 Source = Alexander, I. (2003). Misuse Cases: Use Cases with Hostile Intent.
Source = Alexander, I. (2003). Misuse Cases: Use Cases with Hostile Intent.
So when do we know when to use the misuse case? It is best used when a nonfunctional requirement interfaces with an important mechanism.
 Source = Alexander, I. (2003). Misuse Cases: Use Cases with Hostile Intent.
Source = Alexander, I. (2003). Misuse Cases: Use Cases with Hostile Intent.
There are some trade-offs with misuse cases. For instance, one connundrum is that for every new element added to a system, and thusly to the use case, a new range of misuses must then be accounted for. Once the threats and misuses are identified, new systems, and new use cases must be developed for the solutions to the misuses. The key to understanding the valuation in these trade-offs is understanding the functional and nonfunctional requirements of the system design, being thoughtful and responsible where misuse cases are employed, lest they spiral your seemingly docile use case into an exponential model of trapping and solving for every iteration of possible misuse. Source = Alexander, I. (2003). Misuse Cases: Use Cases with Hostile Intent.
Links back to use cases, or the home page:
Contact Info
James R. Currey
prepared for Prof.Sauter, IS 6840
Email: jrc6d9@umsl.edu